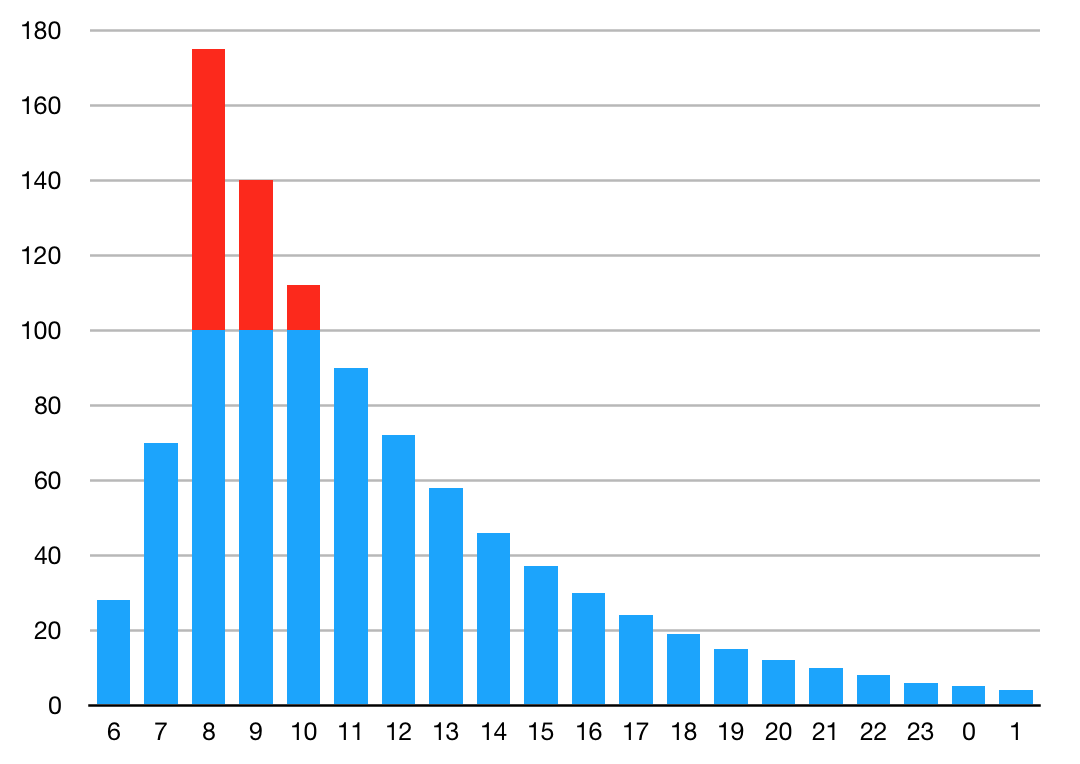
112-storing: hoe voorkomen we zulke problemen op het internet?
▼ Afgelopen maandagmiddag was er een grote storing in het telefonienetwerk van KPN, waarbij ondermeer het alarmnummer 112 zo'n drie uur niet bereikbaar was. Hoe kan het dat een telefoontje op een vaste lijn van KPN naar een meldkamer in de veiligheidsregio Groningen last heeft van dezelfde storing als een telefoontje van een Vodafone-gebruiker naar een meldkamer in de veiligheidsregio Limburg-Zuid? Dinsdag kwam het antwoord: een softwarefout. Het mocht niet baten dat het betreffende systeem viervoudig uitgevoerd was.
Intelligent network
In de telefonie is al vele jaren geleden het zogenaamde intelligent network ingevoerd. Voor die tijd waren vaste nummers gekoppeld aan wijkcentrales en mobiele nummers aan de mobiele operator. Als je dus van de ene kant van de stad naar de andere verhuisde, of van de ene mobiele operator naar de andere, dan kreeg je een nieuw nummer. Met IN was dat niet meer nodig: de telefooncentrale vraag aan een centrale database waar telefoontjes naartoe gerouteerd moeten worden. Probleem is wel dat het telefoonnetwerk nu afhankelijk is van een klein aantal centrale systemen. (En Voice over IP (VoIP) heeft dat versterkt.) Voorheen kon je nog binnen je eigen stadsdeel bellen zolang de wijkcentrale het deed, ook al lag de rest van het telefoonnetwerk plat.
Internetrouters worden afhankelijk van centrale systemen
We zien nu dezelfde ontwikkeling op ons af komen in de internetwereld. Van oudsher zijn we op het internet in het voordeel omdat organisaties zich tegelijk via meerdere service providers aan kunnen sluiten, zolang zij in staat zijn hun eigen BGP-routering te draaien. Maar nieuwe ontwikkelingen zoals SDN, software-defined networking, introduceren afhankelijkheden van centrale systemen. Maar bijvoorbeeld ook RPKI, een systeem om de routering op het internet te beveiligen tegen (onder meer) route leaks. Nu is het zo dat routers van verschillende organisaties routeringsinformatie uitwisselen via BGP, waarbij de routers zelf filters moeten hebben die zorgen dat ze alleen de juiste informatie doorgestuurd wordt. Dat gaat niet altijd goed, waardoor internetverkeer zomaar de verkeerde kant opgestuurd kan worden.
RPKI voorkomt dit door op een centrale plek filters te maken die dan naar de routers gestuurd worden. Aan de ene kant maakt het centraliseren van deze complexe taak en hem uitvoeren op servers die open source software kunnen draaien dit een stuk makkelijker, maar aan de andere kant, als zometeen die filters onmisbaar zijn om het internet te laten functioneren, hebben we het internet afhankelijk gemaakt een klein aantal servers die allemaal gebruik maken van een beperkt aantal softwarevarianten?
Die centrale functies helemaal buiten de deur houden zal niet lukken, want ze hebben enorme toegevoegde waarde en zijn veel makkelijker te implementeren dan regelmatig tientallen, honderden of zelfs duizenden routers van nieuwe functionaliteit te voorzien. Maar: maak je voor kritische functies niet afhankelijk van één softwareversie. En zorg dat routers hun basisfunctie ook op eigen kracht kunnen uitvoeren.
Crisismanagement en wat nu voor 112?
Nog een paar laatste woorden over het crisismanagement bij de 112-storing: dat ging niet bepaald volgens de regelen der kunst. Aan de ene kant begrijpelijk, want als je alles dubbel, driedubbel of zelfs vierdubbel uitvoert met protocollen om automatisch over te schakelen bij uitval, dan kan het eigenlijk niet anders dan dat wanneer het systeem alsnog uitvalt, dit komt door een stomme fout of een totaal niet te voorziene samenloop van omstandigheden. Voor alle te verwachten problemen is immers een backup-lijn/systeem aanwezig.
Aan de andere kant maakt de communicatie over dit incident pijnlijk duidelijk dat er geen enkele rekening gehouden is met mogelijke uitval van 112. Hopelijk wordt hier de juiste les uit getrokken: geen enkel systeem is onfeilbaar, zelfs niet als alle individuele componenten meervoudig uitgevoerd zijn. Als je afhankelijk bent van een softwaresysteem dan is een storing eens per vijf tot tien jaar ongeveer wel het maximaal haalbare. Op hoge toon van de leverancier eisen dat dit nooit meer voorkomt is dus een zinloze exercitie. Meer dan maatregelen om het oplossen van zo'n storing wat te versnellen zit er realistisch gezien niet in.
Het zou dus verstandig zijn als de andere mobiele netwerken de 112-meldkamers kunnen bereiken zonder afhankelijk te zijn van KPN. Daarmee is de kans op een gedeeltelijke 112-storing groter, maar een kans op een volledige 112-storing een stuk kleiner.
En: waarom kunnen we 112 alleen bellen? Voor de meeste gebruikers is hun telefonieaansluiting waarschijnlijk op dit moment (nog) wel betrouwbaarder dan hun internetverbinding, maar als je naast via de telefoon, 112 ook via een website en/of app zou kunnen bereiken, zitten niet langer alle eieren in één mandje.
Permalink - posted 2019-06-25